Cybersecurity Services for Ohio-Based Businesses
About Cloud Cover's Cybersecurity Services
We provide cybersecurity consulting services and support for Columbus, Central Ohio, and beyond. We provide Managed Cybersecurity as a Service for your business for a predictable monthly cost.
Our local team of security experts monitor, manage, and help you prevent cyber-attacks to keep your business and critical data safe and secure.
Have specific compliance needs? We can tailor our solutions to help you get compliant and stay compliant.
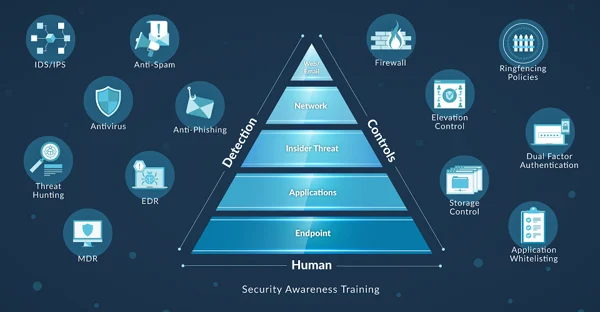
What Cyber Security Services Do We Provide
-
Phish Testing and Training
-
Multi-Factor Authentication
-
Dark Web Scans
-
Cyber Security Insurance Consultations
-
IT and Cybersecurity Compliance
-
Ransomware Prevention and Remediation
-
Zero Trust Security
-
Email Security
-
Incident Response
-
Penetration Testing
-
Data Loss Prevention
-
Managed Backups
-
Submit Question
Cybersecurity Services Inquiry
Cyber Security Planning
What makes a good cyber security plan for small businesses?
-
Spam Filter
-
Phishing testing and training
-
DNS Filtering
-
Internet Filtering
-
Device Configuration
-
Backups
Everyone know a spam filter is important. However, it's also important to move beyond the basics with services such as Microsoft Advanced Threat Protection.
Inadequate cybersecurity training can have serious financial consequences. The most effective form of training involves short 2-3 minute videos sent to employees after they click on a fake phishing link.
DNS filtering is the process of using the Domain Name System to block malicious websites and filter out harmful or inappropriate content.
Internet content filtering can and should be performed at multiple layers. Content filtering allows you to block certain categories of websites based on your organizational policies. It also filters malware.
Hardening devices makes a different in whether or not an attack succeeds and how fast it can spread. Following a standard like the Center for Internet Security is a good place to start.
Backups are the last line of defense. They are formally included in the NIST (National Institute of Standards) frameworks. You can read more about the NIST Cybersecurity Center of Excellence here. There are many types, brands, flavors and permutations of backups.
Cybersecurity Insurance
There are two main types of cyber insurance options available to businesses: first-party cyber insurance and third-party cyber insurance. First-party cyber insurance is designed to protect the business itself against losses caused by a data breach or other cybersecurity incident. This type of insurance covers the business’s own costs related to the incident, such as forensics investigation costs, business interruption losses, and related reputational damage. Third-party cyber insurance focuses more on protecting the business from legal liabilities associated with a cybersecurity incident. This type of coverage will provide protection for claims made against the company by customers, vendors, or other third parties alleging financial loss due to an incident, as well as cover legal costs associated with defending those claims.
How much cyber insurance coverage do you need?
This is a personal decision for each business owner to make. Start with these questions when preparing to talk to your insurance agent.
-
What does it cost your business to be down for a day?
-
How long would it take you to rebuild your IT systems from scratch?
-
What would the harm be to your reputation if you lost client information?
-
Are you spending enough on good quality security now? Security spend should be about 25-50% of your overall IT budget.
-
Do you train your employees?
-
Do you regularly review phishing test results?
-
Have you talked with your peers? A business owner once told us he was the only one in his peer group that hadn't suffered through a ransomware attack.
Email Security
Protecting your emails from cyber threats is essential. Not only does it protect the sensitive information of your customers and employees but also maintains the integrity of your brand. You'll need to secure your Office365 environment AND your devices. Many businesses are hesitant due to cost or lack of understanding of what's involved. Understanding how to secure your email is complicated. Understanding how to work with someone to secure your email is not. And, the cost is small relative to other IT investments. Your Microsoft Secure Score is a good place to start.
We can help manage your licensing and decide what layers to put in place to secure your email.

Phishing
Roughly 90% of attacks start with a phishing email. The most effective defense against phishing is training. Phishing training can be as short as 2-3 minute videos presented to employees right after they fail a test.
Types of Phishing Attacks
-
Email Phishing
-
Smishing
-
Spear Phishing
-
Angler Phishing
-
Whaling
-
Search Engine Phishing
IT Compliance
IT compliance isn't just for large corporations. Compliance programs help small businesses adhere to best practices which protect sensitive data and ensure business continuity.
Avoiding Legal Consequences
Non-compliance with IT regulations can result in hefty fines and penalties, which can have a significant impact on a small business's financial health.
Protecting Sensitive Data
Compliance helps businesses take measures to protect sensitive data, such as customer information and financial data, from cyber threats and data breaches.
Meeting Customer Expectations
Compliance regulations help businesses demonstrate their commitment to protecting customer data, which can help build trust with their customers.
Boosting Business Efficiency
Compliance ensures businesses have proper data management, IT security, and disaster recovery plans in place. Complying with best practices help small businesses improve their efficiency, reduce IT risks, and ensure business continuity in case of unforeseen events.
To learn more about our IT and Cybersecurity Compliance Services, check out our page.
Data Loss Prevention
Data loss prevention (DLP) is a strategy for protecting confidential or sensitive information from unauthorized access. It involves identifying, monitoring, and protecting data in transit and at rest. DLP solutions can monitor and protect data stored on hard drives, cloud storage systems, email servers, networks, and other connected devices.
DLP adheres to the Pareto Principal. A relatively small amount of work can get you most of the benefits. You may already be paying for DLP features in your Office 365 plans.

Zero Trust
Zero Trust is a combination of "never trust, always verify" combined with "least access." Traditional security assumed if you were in the building you were allowed to go where you wanted. Zero Trust is the digital equivalent of locking the interior doors. The goal is to prevent unauthorized access to data and services. Zero trust may require a change in an organization’s philosophy and culture around cybersecurity.
Identity |
Device |
Network |
Application |
Data |
|---|---|---|---|---|
Traditional |
||||
Passwords |
Basic Inventory |
Flat network |
On-prem |
File permissions |
Zero Trust |
||||
MFA SSO |
Compliance Enforcement |
Segmented Network |
Cloud Based SSO |
Encryption DLP |
Zero trusts move from passwords to MFA and Single Sign-On. MFA provides a higher degree of confidence that it's you rather than a hacker sitting in a dark room pretending to be you. Single sign-on formalizes the concept of identity rather than separate systems that just consider a username and password. SSO works based on a trust relationship established between the party that holds the identity information and can authenticate the user and the service or application the user wants to access. It's the electronic version of a driver's license. Other businesses trust your license is valid and in effect trust the State of Ohio to verify your identity more than they would trust themselves to verify your identity.
Click the button to learn if Zero Trust strategies are appropriate for your business.
Multi-Factor Authentication (MFA)
Everyone understands the important of MFA. Everyone uses MFA to access their back accounts and email. Most owners and managers don't have a grasp on what percentage of their applications are protected by MFA or what it would cost to add protection to a system.
-
MFA Can Help You Be Compliant: Many industry regulations, such as HIPAA and PCI-DSS, require the use of MFA to protect sensitive data. By implementing MFA, small businesses can comply with these regulations and avoid costly fines and penalties.
-
MFA is Cost-Effective: Implementing MFA is relatively low cost and can provide significant security benefits. Many MFA solutions are cloud-based, which means there is no need to invest in additional hardware or software.
-
MFA is User-Friendly: MFA solutions are easy to use and can be customized to meet the needs of your business. Many solutions offer a variety of authentication options, such as text messages, biometric scans, or push notifications, allowing users to choose the option that works best for them.
Ransomware Prevention
Ransomware Prevention Checklist
-
Provide training to employees.
-
Run phishing tests.
-
Insist on MFA— Everywhere.
-
Observe and participate in backup and disaster recovery testing.
-
Review cyber insurance applications.
Ransomware Prevention
If you think you have fallen victim to ransomware attack, first— don't panic. Second, don't deal with this alone. If you think you might be infected by Ransomware, we can help. Let us assess the situation and help you decide the best course of action. We have helped many companies get out of paying, get their data back, or pick up the pieces if it's just too late. Don't do this alone— contact us.
Penetration Testing
A penetration test, often referred to as a “pentest,” is a human or group of humans performing an authorized simulated attack on a computer system, network, or web application to evaluate its security posture. The process is used to identify potential vulnerabilities and misconfigurations that could be exploited by malicious actors.
Many times, "vulnerability scan" and "penetration test" are used interchangeable. They are very different things in terms of cost and the information they provide.
How is a penetration test different than a vulnerability scan?
Which one do you need?
What does it cost?
Isn't there a less expensive option?
Dark Web Scans
A dark web scan is a process that searches the dark web for any compromised company data. The dark web is a part of the internet that is not accessible through traditional search engines, and it is often used by cybercriminals to sell or trade stolen data. A dark web scan can detect early signs of a data breach, allowing you to take immediate action to prevent further damage. By regularly scanning the dark web, you can monitor if any of your business's sensitive information is being traded or sold.
A dark web scan is an effective and affordable tool for small businesses to detect and prevent data breaches. It can help protect your business's reputation, comply with industry regulations, and provide comprehensive monitoring of compromised data. By implementing a dark web scan, small business owners can mitigate the risk of data breaches and safeguard their businesses against potential losses.
Incident Response Planning
"I have always found that plans are useless, but planning is indispensable."
Dwight D. Eisenhower
Most plans have these seven elements in them. It's not necessary to have all of these elements and many aspects will not be feasible for companies without large in-house IT teams. Some elements like preparation are absolutely the responsibility of business owners and require your specific knowledge to complete. No IT company or even IT employee knows as much about different parts of your business as you.
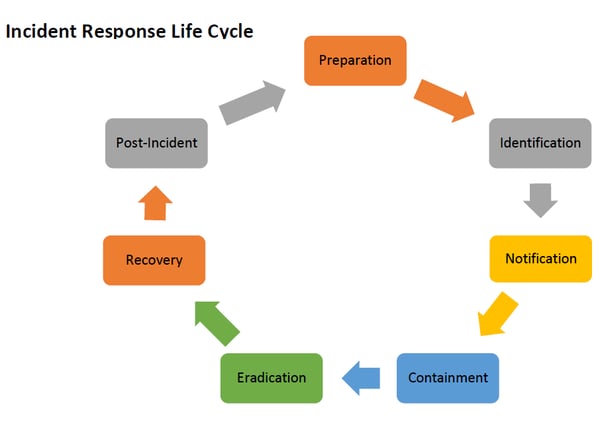
Preparation
Identification
Notification
Containment
Eradication
Recovery
Post-incident Activities
Learn more about Incident Response Plans and how to create yours here.
Your Business Needs a Cybersecurity Policy.
Get Your Free Template Now.
Proud to Be Local. Areas We Serve in Ohio
Columbus Metro Area Including:

Pickerington

Worthington

Dublin

Westerville

Gahanna

Pickerington
Outside of Columbus
Also providing remote Cybersecurity services throughout the Midwest.

Lancaster

Newark

Zanesville

Athens

Mansfield

Lancaster
Think your Ohio business has been the victim of a cyberattack?
Don't wait, we can help.

