Ransomware Prevention: A Layered Approach
Jump to how business owners and managers can prevent ransomware
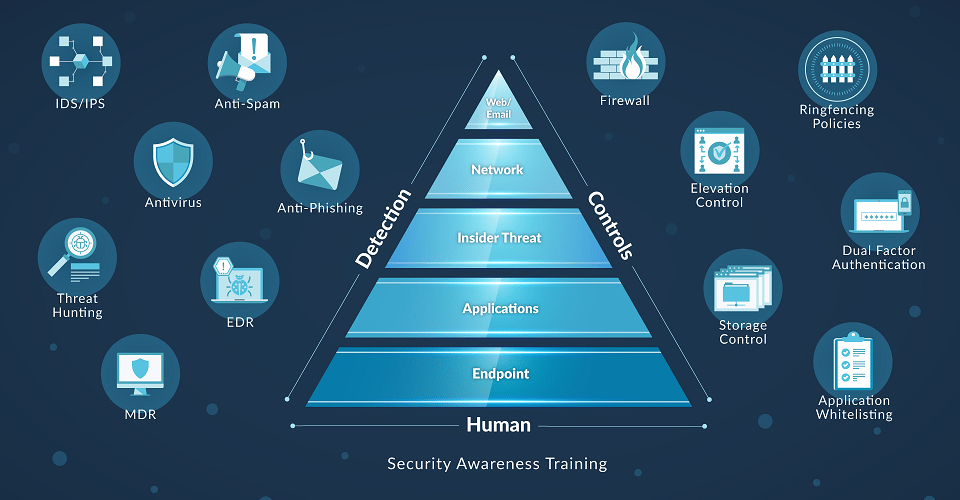
Historical Perspective of IT Security
Each time a new attack is found, technology companies develop a new product to detect and prevent that attack. This strategy worked well for a time. In the 1990’s security measures were focused on controls such as firewalls and internal policies. By the early 2000’s, antivirus protection was a must. A new worm or Trojan arose and antivirus professionals quickly developed and sent us a method to detect it and stop it before it damaged our systems. But by 2005, attacks shifted from causing chaos to data theft and ransom. Additionally, the volume of attacks grew substantially. Over 5 million new malware samples were being found annually.
So what did marketing departments everywhere do? They renamed their product as "NextGen endpoint protection" because legacy antivirus wasn’t keeping up. Unfortunately, by 2010 it was clear that cyber attacks were becoming a business model. Keyloggers were running rampant getting bank information. Fileless malware and more targeted attacks became the norm. Technologies like endpoint detection and response (EDR) were developed and added to the security stack.
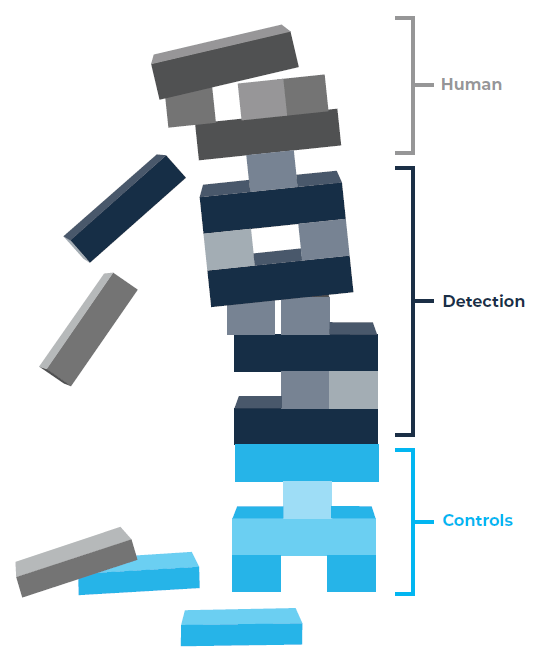
By 2015, IT teams were buried in alerts and security operations centers (SOC) were formed to manage alerts. SOC analysts were reactionary and trying their best to find issues and stop invaders before they caused irreparable damage. The end result is a teetering tower of protection.
Modern Ransomware Prevention
In 2011, Lockheed Martin published its Cyber Kill Chain framework. The model describes steps attackers go through in order to breach, destroy or gain control of systems. Modern Ransomware Protection attempts to interrupt attackers at each phase in their process by using software, policies and education.
7 steps of the Lockheed Martin Cyber Kill Chain
Reconnaissance |
Attackers gain knowledge of their target by gathering information such as system architecture, configurations, user profiles, open ports, etc |
|---|---|
Weaponization |
Attackers select or create malicious code or payloads to be delivered in order to exploit the target system. |
Delivery |
After weaponizing the attack, attackers deliver it to the target through a direct connection or via email or other means of communication. |
Exploitation |
The attacker attempts to exploit any vulnerabilities found in the target system using the malicious code delivered in the previous step. |
Installation |
The attacker then installs malicious components on the compromised system in order to gain persistent access for future attacks and/or data exfiltration purposes. |
Command and Control |
Malicious components installed on the compromised system are used for remote control and/or further exploitation of the system by attackers who have gained access from outside locations using various techniques such as botnets, tunneling protocols, etc. |
Actions on Objectives |
Once attackers have achieved their objectives — such as data theft or ransomware deployment – they use their access points in order to execute those actions across multiple systems within a network that can result in massive damage and disruption of business operations if not detected soon enough. |
Stopping attacks at each step
At each step along the way, the goal is to interrupt the attacker. Below are some examples of how security professionals attempt to stop attacks using various pieces of software, hardware and training to protect different types of infrastructure.
Reconnaissance |
Firewalls block port scans Intrusion Detection Systems block the source of the traffic Applications authenticate an account before providing information Employees are taught not to click on links in phishing emails or answer questions from unknown callers |
|---|---|
Weaponization |
Event Detection and Response software looks at patterns and flags suspicious activities Zero Trust enforcement software blocks unknown or altered software |
Delivery |
Spam filters stop delivery via email Configuration policies block the use of USB drives |
Exploitation |
Security patches are applied regularly Vulnerability scans attempt to find gaps before attackers can Applications re-authenticate periodically to limit attacks |
Installation |
Data Loss Prevention (DLP) limits the damage from exfiltrated data Zero Trust enforcement software blocks unknown or altered software Computer policies and permissions should stop software installation |
Command and Control |
The firewall attempts to detect and block command and control traffic at the network level EDR software attempts to detect and block command and control traffic at the computer level SIEM tools look for patters in network traffic to detect the attack |
Actions on Objectives |
DLP limits the damage from exfiltrated data EDR software tracks and prevents the spread of malware from PC to PC |
How can business owners prevent ransomware
Provide training to employees.
-
Training should be tracked
-
Training should have both an on-line self paced and in person components
-
Short 2-3 minute online training sessions often work better than longer once a year sessions
Run phishing tests
-
Review the results of phishing tests in management meetings and with employees
Insist on MFA
-
Use MFA on all of your own accounts
-
Have your MSP force MFA on all systems where it is available
-
Use MFA and security options as a criterion when selecting new software and systems
Observe and participate in backup and disaster recovery testing
-
Mandate backups be tested at least quarterly
-
Dedicate at least one hour a year to one of the most critical components of your infrastructure
-
Participate for 10-15 minutes per quarter in backup testing
-
Observe if your IT person is having an easy time with the restore or is frustrated
-
Observe if the test completed in the amount of time you expected
Review cyber insurance applications
-
The applications should not simply be handed to your employees or MSP to fill out Ask what layer of your security each item on the application addresses
More ransomware prevention resources
Specifically: Ransomware Response Checklist and the Ransomware Guide
