Penetration Test Answers and Examples
What is a penetration test
A penetration test, often referred to as a “pentest,” is a human or group of humans performing an authorized simulated attack on a computer system, network or web application to evaluate its security posture. The process is used to identify potential vulnerabilities and misconfigurations that could be exploited by malicious actors. This type of assessment provides detailed and comprehensive results because it looks beyond known vulnerabilities to uncover gaps or misconfigurations that could be exploited by malicious actors.
What is a vulnerability scan
A vulnerability scan is an automated process that examines a system for known weaknesses in order to detect exploitable issues. This type of assessment is typically done quickly, providing a snapshot of the security state of the system. The results, however, are limited since only known vulnerabilities are tested for.
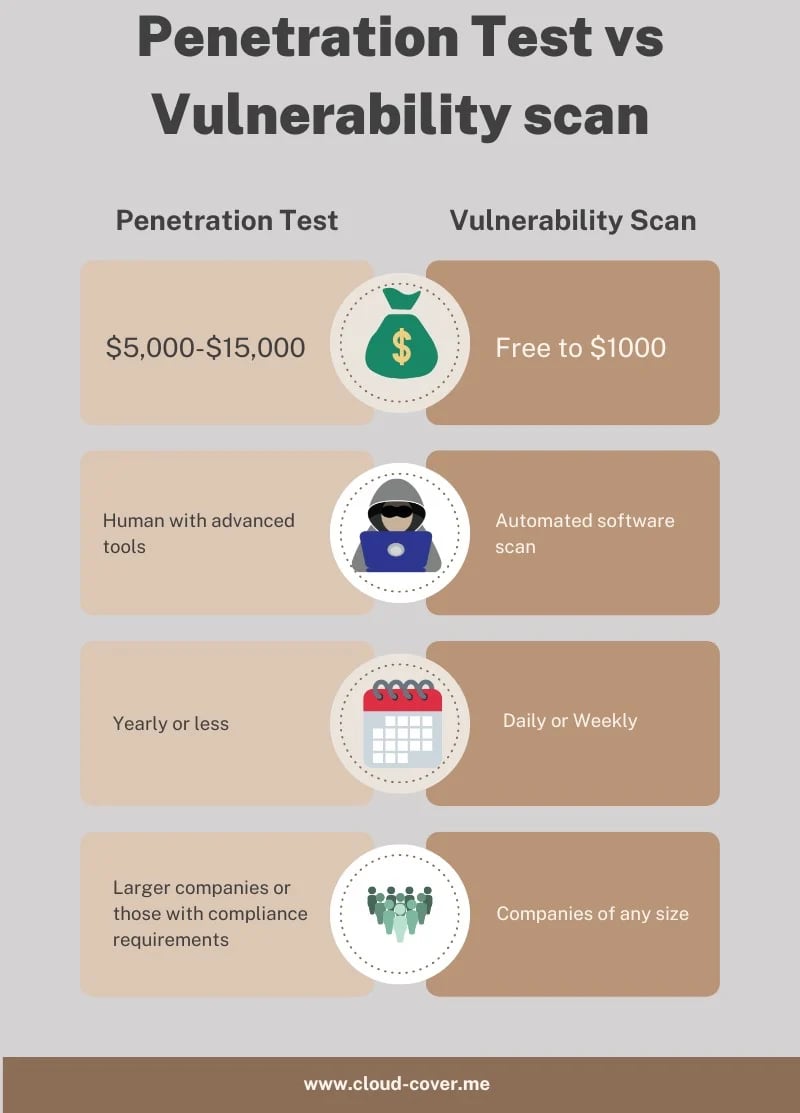
How is a penetration test different than a vulnerability scan?
A penetration test and a vulnerability scan are both commonly used security assessments that can help organizations identify potential vulnerabilities in their environment. Most of the time, when people talk about a penetration test they are really talking about a vulnerability scans. Many "penetration testing" services are often selling $5,000 vulnerability scans. One is a detailed and thorough exploration for flaws. One is a check for obvious oversights or misconfigurations.
Which one do you need
In the absence of compliance requirements, regulations or customer requirements, the answer is almost always a vulnerability scan. They're free or close to it and help you identify the most common security risks.
What kinds of penetrations tests are there
There are various types of penetration tests that an organization can use to assess its security posture. These include black box testing, white box testing, gray box testing, application-level penetration tests and network-level penetration tests. Black box testing is a method of evaluating the security of a system without any prior knowledge about its internal workings or architecture. White box testing involves detailed knowledge about the system's architecture in order to identify vulnerabilities and misconfigurations within it. Gray box testing combines elements from both black and whitebox tests by providing some information on the target system while still allowing for exploratory attacks on unknown parts of the environment. Application-level penetration tests focus on individual applications such as web browsers or email clients while network-level tests involve analyzing an entire network infrastructure for potential weaknesses or exposures. By combining these different types of pen tests into one comprehensive assessment, organizations can gain invaluable insights into their overall security posture and take measures to mitigate future risks.

The problems with a penetration scan (other than cost)
If you read the fine print for a penetration test, most companies spend pages detailing how they're not responsible for anything that breaks during the process. Think of paying someone to test the strength of your front door. To know exactly how strong the door is they have to keep attacking until it breaks. Only after it's broken can you really know how strong it was.
Fun examples and findings from reports
Vulnerability scan examples
-
All internet connected webcams
-
All Blue Iris web cams
-
All remote desktop servers
-
All Network Attached Storage (NAS) devices
Hackertarget.com is an easy to use service that can scan your networks from the outside. It will identify common issues and it can alert on changes. This is useful in cases where a tech makes an inappropriate change to a firewall.
Penetration test example
The version of Mozilla Firefox installed on the remote Windows host is prior to 57.0.4. It is
therefore vulnerable to a speculative execution side-channel attack. Code from a
malicious web page could read data from other web sites or private data from the
browser itself.
It is recommended you upgrade Oracle Java SE 1.7.x < 1.7.0_211 / 1.8.x < 1.8.0_201 / 1.11.x < 1.11.0_2 Multiple
Vulnerabilities (January 2019 CPU): Upgrade to Oracle JDK / JRE 11 Update 2, 8
Update 201 / 7 Update 211 or later. If necessary, remove any affected versions.