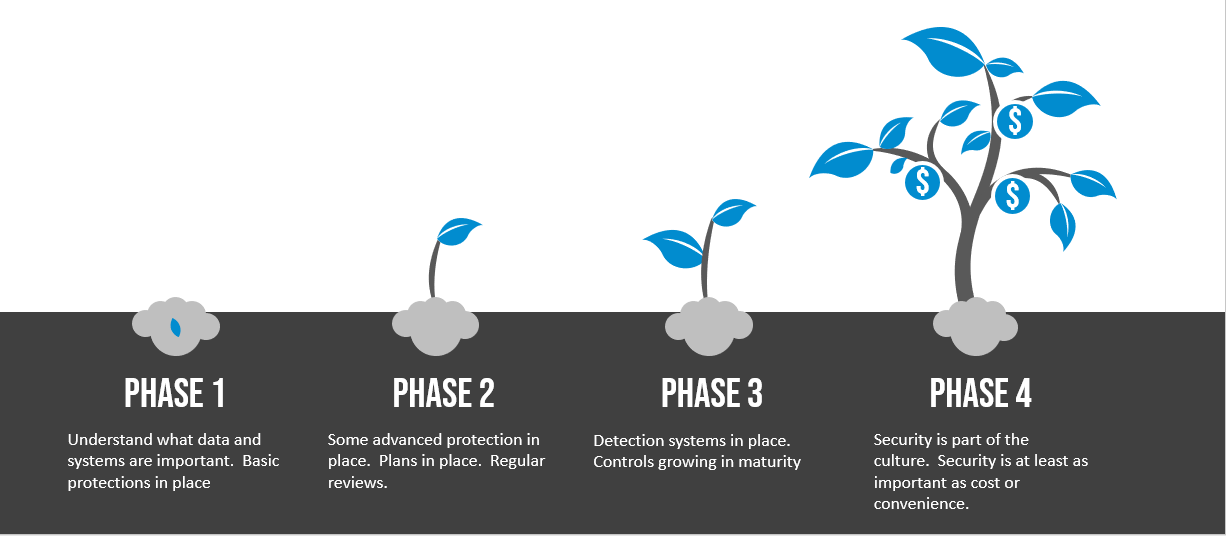
Small Business Cybersecurity Plan
What makes a good cyber security plan for small businesses?
Your cyber security plan should include multiple layers of security. You plan isn't a one time project but a continuous journey. Consider how malware could reach your data and what can be done along the way. Physical security for your home or business is a good analogy. You might have a gate and a "protected by alarm company" or beware of the dog sign to deter attackers. You lock your door to slow them down. You might let your neighbors know when you go on vacation and turn on your alarm system to let you know in case something happens.
Spam Filter
Everyone know a spam filter is important. However, it's also important to move beyond the basics with services such as Microsoft Advanced Threat Protection.
It's important to scan links in emails as they arrive....it's also important to re-scan the links a week later if the email is opened again. It's common for attackers to replace a healthy file with an infected one to try and bypass a one-time scan.
It's important to have a sandbox feature that tests for suspicious behavior as well as basic viruses. Should that Excel file from your accountant really try and send traffic to Russia when it's opened?
Phishing testing and training
Inadequate cybersecurity training can have serious financial consequences. The most effective form of training involves short 2-3 minute videos sent to employees after they click on a fake phishing link. The training should be short enough so they they'll watch it, delivered soon enough they remember what happened and informative enough they understand what they should have noticed.
Read more about phishing here
DNS Filtering
DNS filtering is the process of using the Domain Name System to block malicious websites and filter out harmful or inappropriate content. Your computer converts every website into an IP address and uses that address to find the website. DNS filtering is the modern equivalent of directory assistance refusing to provide you a phone number for a business it thinks is suspicious.


Internet Filtering
Internet content filtering can and should be performed at multiple layers. Content filtering allows you to block certain categories of websites based on your organizational policies. It also filters malware. It also identifies suspicious traffic and can help to identify which device on the network is sending the traffic. Most anti-virus software includes content filtering...but it only works if the software is installed. Coporate anti-virus software isn't installed on employee owned devices, mobile devices, copiers, security cameras, etc
Device Configuration
Hardening devices makes a different in whether or not an attack succeeds and how fast it can spread. Following a standard like the Center for Internet Security is a good place to start. The standards can be technical and time consuming to implement so from a business perspective the best thing to do is to ask your current or perspective MSP what standards they follow and how they implement those standards. The CIS Benchmark for Windows 10 is 1245 pages. So, if you ask your MSP how these secure your computers and they respond with a 1 page answer....you know there's work to be done.
Event Detection and Response (formerly anti-virus software)
Traditional antivirus software is designed to detect and block malicious threats, such as viruses and malware. It scans for known signatures, scanning the system for files or processes that have known malicious behaviors associated with them. Event detection and response (EDR) software is a more sophisticated approach to security, providing organizations with the ability to detect, investigate, and respond to advanced attacks in real-time. Unlike traditional antivirus software, EDR solutions leverage artificial intelligence (AI) technologies to automatically detect anomalous activity by analyzing system behavior in order to identify potential threats.
There is a massive amount of difference between traditional AV software and modern EDR software in terms of the amount of data they provide. In this example multiple PCs are shown, the type of attacks are shown and so is information that can be used for cross-reference with firewall logs.
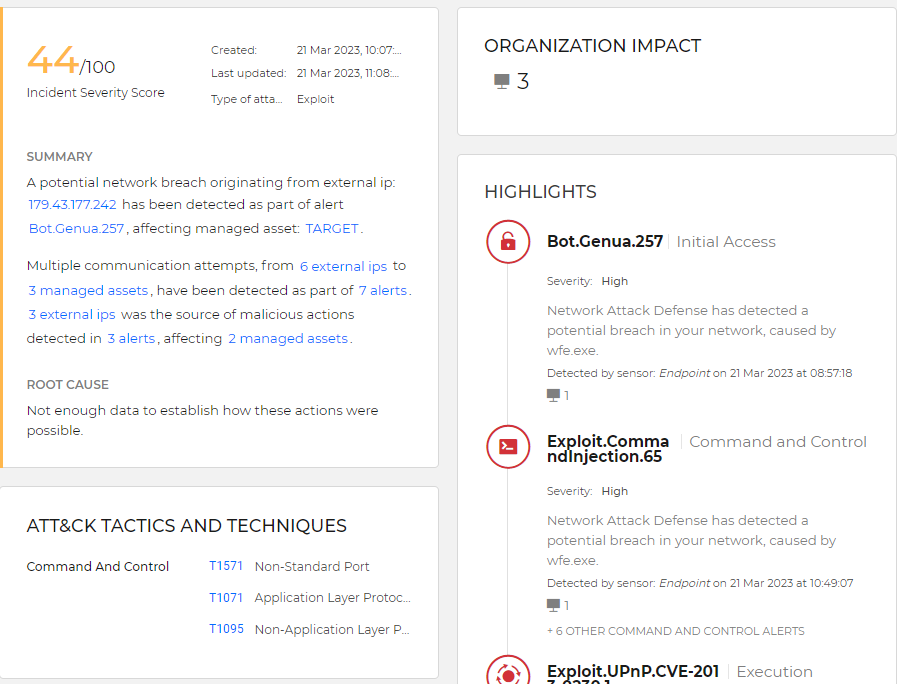
Event Detection and Response
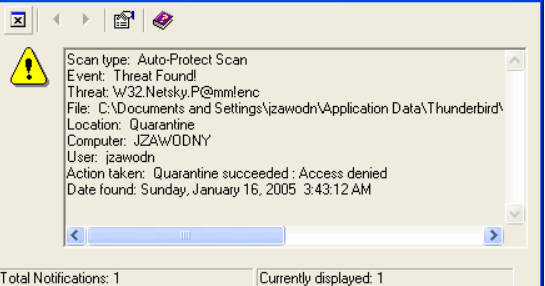
Traditional AV
Backups
Backups are the last line of defense. They are formally included in the NIST (National Institute of Standards) frameworks. You can read more about the NIST Cybersecurity Center of Excellence here. There are many types, brands, flavors and permutations of backups.
NIST provides a Guide for Managed Service Providers to Conduct, Maintain and Test Backups Files. This would be a good document to download and review with your IT company.
All backups should have a few basic characteristics.
-
Multiple copies in different locations
-
Different storage media or cloud services
-
Encryption
-
Separate passwords. The same passwords (like a domain administrator account) should not be able to access both the data and the backups.
-
They are tested
For any backups, you should understand and accept both the RPO and RTO:
-
RPO refers to the amount of data that you are willing to lose in the event of a disaster. It is the time that can pass between your last backup and the disaster occurring, without losing more data than you are willing to accept. For example, if your RPO is 1 hour, it means that you can only afford to lose up to 1 hours’ worth of data in the event of a disaster. So, if your last backup was taken 3 hours ago and disaster strikes, you could lose up to 3 hours' worth of data. Some people backup nightly and some hourly.
-
RTO refers to the amount of time it takes to restore your data after a disaster has occurred. It is the maximum amount of downtime you are willing to accept before your systems are back up and running. For example, if your RTO is 4 hours, it means that your systems must be restored within 4 hours after a disaster has occurred, in order to minimize the impact on your business operations. If you need to be back up and running in a few minutes, we can do that with a second physical server and constantly pre-stage restores there. If you can be down for a day, we could plan to fix the existing hardware and recover to it.
As an owner or manager responsible for IT, it is your responsibility to:
-
Understand (at a very high level) the backup process
-
Know your RPO and RTO
-
Confirm backups are tested
Next steps
Where do you go from here? Subscribe to our IT Compliance for Non-Technical Managers blog for more information. Remember, security is a journey.