Incident Response Plans for Small Business
A word of caution - the word incident has specific meanings in the legal and insurance industries. It's safest to avoid the word outside of planning.

If your incident response plan is longer than two to three pages, you need a shorter response plan
Things to know about incident response planning
-
Your insurance policy has conditions
You cyber insurance policy almost certainly has a few sentences worth of requirements that should be highlighted in your plan. Almost all insurance plans have requirements of informing your insurance company BEFORE you start trying to fix an issue. Failure to follow their procedures could result in them not paying your claim if you have to make one. - Make sure your IT person or company is aware of conditions in your insurance policy
Your IT person or MSP is there to help. Make sure they know there are times they need to call the insurance company first. - Begin with the end in mind
Writing an incident response plan is as much about what you do before an incident as it is what you do after an incident. Installing a security camera after the incident won't help you get it on video. Once you have a list of incidents that might happen think about prevention. - Test your plan
The problems with most incident response plans
The biggest problem with most response plans is they are overly formal and much too long. What you do not want in the event of an emergency is a fifteen pound one thousand page binder. You want clear concise instructions on what do to next. There is good reason the number you call in emergencies is 911 and not distributed as a ten page pamphlet with a flow charge that guides you through what type of emergency you are having and provides individual numbers for the poising control center and fire department broken out by county.
Most incident response plans include a lot of definitions. This is helpful only in the case of a slow calculated response coordinated across a large team of people or if your emergency is hypothermia and you need to start a fire for warmth. In an incident where someone has stolen your information you need to know what to do next not a definition to classify exactly what kind of information is stolen.
Incident response vocabulary to help you read more online
-
Incident: An incident refers to any event that has the potential to disrupt the confidentiality, integrity, or availability of information or information systems. Examples of incidents in cybersecurity include unauthorized access to a system, data breaches, malware infections, or phishing attacks. An incident response plan outlines the steps you should take to detect, contain, and mitigate the incident. It also includes guidelines for communicating with your IT company, insurance company and customers.
-
Accident: An accident, refers to an event that occurs by chance or unintentionally. In cybersecurity, an accident might occur if an employee accidentally deletes important data or misconfigures a system.
-
Emergency: An emergency refers to a situation that requires immediate attention and action. In cybersecurity, emergencies might include situations like a ransomware infection. A more general example would be a server that won't power on and stops your company from working.
- Disaster response plan: A disaster recovery usually refers to how you will recover data or a server if it is lost. Sometimes, it refers to how you will operate during a disaster like working out of a second office if there's a fire or working from home during Covid. It outlines procedures for backup and restoration of data and systems, the allocation of resources, and the restoration of services.
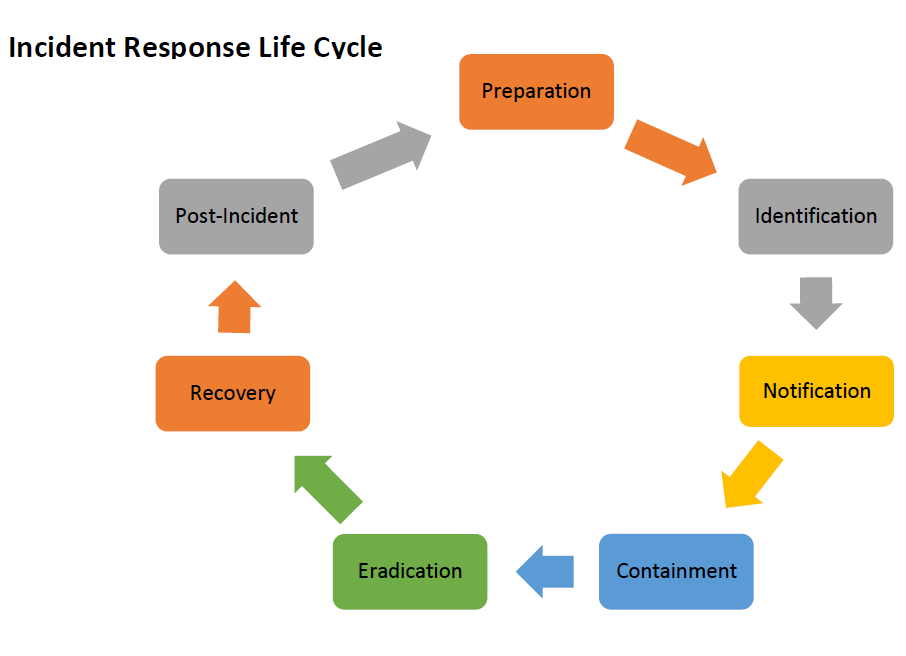
What goes into an incident response plan
Most plans have these elements in them. It's not necessary to have all of these elements and many aspects will not be feasible for companies without large in-house IT teams. Some elements like preparation are absolutely the responsibility of business owners and require your specific knowledge to complete. No IT company or even IT employee knows as much about different parts of your business as you.
-
Preparation
-
Identification
-
Notification
-
Containment
-
Eradication
-
Recovery
-
Post-incident Activities
Preparation
-
Practice exercises (aka Table-top Exercises)
-
Where is the plan kept (Hint: print it out. you can't print the plan after the ransomware encrypts the document)
-
Is there a policy that could have prevented an issue? Make it now.
-
Is there a software or system needed to help resolve the issue? i.e. do you need one more camera or a spare server?
-
What will the warehouse employees do without a system to tell them which orders to pick
-
How will you pay bills if your accounting system is down for a day, a week or two weeks
Identification
-
What could go wrong? Losing a server, power outage, fire, ransomware, etc
-
Who needs to be included in your plan? MSP, insurance company, customers
Notification
-
How will you contact your employees? Do they answer their phones at 1AM?
-
How will you notify customers if you hundreds or thousands of them?
Containment
-
Get the right insurance coverage in advance
-
Does your industry have required reporting where you will have to inform your clients of a breach?
Elimination of the threat
-
How do you know the threat is over? It's common for people to allow users back into systems after a ransomware attack and have the files re-encrypted.
-
If you wipe all your PCs, do you have the needed software installation files so your accounting, bidding or WMS systems can be re-installed
Recovery
-
How will you restore your operations. How long will it take? Will you lose an hour or a week's worth of data.
Aftermath
-
How will you let clients know you're operational again
Write your own incident response plan step by step
Add the basics
- Add a note remind employees reading the plan not to speak to clients, insurance companies etc until authorized to do so. It's likely they don't know all the facts
- Remind everyone not to begin working on an infected or breached system until the insurance company has been consulted
- Review your cyber insurance policy to see if the insurance company requires you to call a specific security company or declare an incident etc. Add names and phone numbers to your plan.
- Document phone numbers for managers, IT staff, MSP after hours, etc. Keep in mind you may not have access to your computer when this information is needed.
- Remind whoever is reading this plan to document as much as possible. No matter how good of a note taker they are the notes will never be complete enough for your insurance company, your attorney or law enforcement.
Who discovered or reported the incident?
When was the incident discovered or reported?
Where was the incident first discovered or located?
What impact does the incident currently have on business operations and what is the scope?
Has the incident source been discovered or is there a suspected point of entry?
- Document basic information that should be preserved (depends on what happens)
Security camera footage
Office 365 sign in logs
Phone records - Build likely scenarios and your response
Ransomware
-
Wipe laptop through InTune
-
Change o365 password
-
Change password for system X
-
Change password for system Y
Lost Laptop
-
Disable network wired and wireless network access on infected computers
-
Remove network cables from servers
-
Call MSP
-
Unplug as many computers as possible
Lost Laptop
-
Check all users have MFA
-
Deploy a DLP (Data Loss Prevention) solution
Ransomware
-
Phishing testing for employees
-
Confirm appropriate insurance coverage
-
Call MSP
-
Unplug as many computers as possible
Common items people wish they had included
-
Increasing Office 365 log retention
-
Deploy a DLP (Data Loss Prevention) solution
-
Deploying a DLP solution
-
Deployed a Zero Trust solution
-
Reviewed their insurance policy with their MSP
-
Tested their backups
-
Confirm backups were isolated from the rest of the network
