
What is Zero Trust Security
- What is Zero Trust Security?
- Is it appropriate for my business?
- The Five Pillars of Zero Trust Security
- Examples of Zero Trust Security in action
- Challenges and potential drawbacks of implementing Zero Trust Security
What is Zero Trust Security
Zero Trust is a combination of "never trust, always verify" combined with "least access." Traditional security assumed if you were in the building you were allowed to go where you wanted. Zero Trust is the digital equivalent of locking the interior doors. The goal is to prevent unauthorized access to data and services. Zero trust may require a change in
an organization’s philosophy and culture around cybersecurity.
Zero trusts moves from passwords to MFA and Single Sign-On. MFA provides a higher degree of confidence that it's you rather than a hacker sitting in a dark room pretending to be you. Single sign-on formalizes the concept of identity rather than separate systems that just consider a username and password. SSO works based on a trust relationship established between the party that holds the identity information and can authenticate the user and the service or application the user wants to access. It's the electronic version of a driver's license. Other businesses trust your license is valid and in effect trust the State of Ohio to verify your identity more than they would trust themselves to verify your identity.
Older security paradigms used a simple asset inventory to track devices. Zero Trust will not only verify the identity of the device but also verify the device is compliant in terms of having up to date patches and and anti-virus software before allowing access.
Zero Trust encourages network segmentation. Servers are separate from phones which are separate from client PCs. It's expected and necessary for a PC to access a server. It's suspicious when one PC is trying to communicate directly with a different PC. It's the on-line equivalent of driving the wrong way down a one way street.
In the past, the server would attempt to authenticate the username and password of the person trying to access an application. Now, the verification will go both ways. The person who just got pulled over for driving the wrong way now wants to authenticate the police officer who pulled them over.
With traditional file permissions, once someone had access to a file they could copy it to a thumb drive and take the data with them. Services like Microsoft Office will automatically encrypt and decrypt data as it's accessed. The encrypted document will open as normal on a company owned device and will prompt for a username and password when someone tries to open the file off a thumb drive. Traditional passwords are finding a needle in a haystack. Encryption is like finding that same needle somewhere in the Pacific Ocean.
Identity |
Device |
Network |
Application |
Data |
|---|---|---|---|---|
Traditional |
||||
Passwords |
Basic Inventory |
Flat network |
On-prem |
File permissions |
Zero Trust |
||||
MFA SSO |
Compliance Enforcement |
Segmented Network |
Cloud Based SSO |
Encryption DLP |
Is Zero Trust appropriate for your business
Probably.
When done correctly if offers a lot of benefits.
Single sign-on increases employee productivity by reducing the time they must spend signing on and dealing with passwords. Employees need access to many apps throughout their workday, and they have to spend time logging in to each of them, plus trying to remember which password goes to which, plus changing and resetting passwords when one is forgotten. The wasted time adds up.
You might think that SSO is the same as just using the same password for all the systems - which is bad. However, the reality is that with good practices, SSO significantly decreases the likelihood of a password-related hack. Since users only need to remember one password for all their applications, they are more likely to create solid, complex and hard-to-guess passphrases.
Nearly 50% of helpdesk calls are password or logon related. Fewer passwords to remember means reduced costs.
Data encryption and Data Loss Prevention improve your security and protect your data in ways that traditional security cannot.
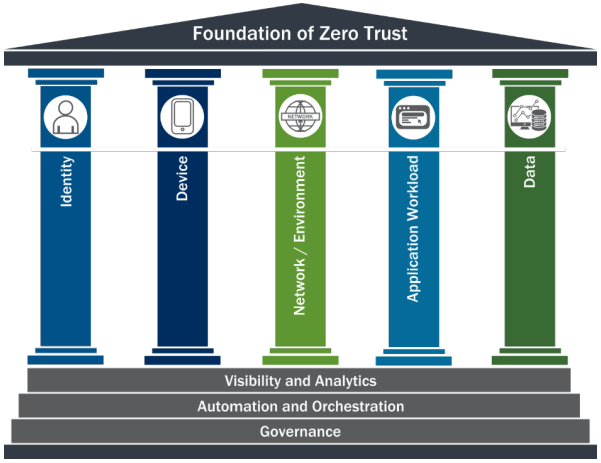
The Five Pillars of Zero Trust Security
There are many paths to Zero Trust. The goal is not zero trust or some trust. It's continual process improvement over time. Each pillar depends on data, automation and governance. In stead of manual configuration of devices, they are configured by policies AND those systems verify configuration before allowing the connection. That's a big AND. Instead of trust...it's trust but verify. There may also be policies that isolate non-compliant devices. i.e. if you connect a computer that has a virus to the network the network itself may turn off ports on switches or kick the computer off the wifi. Traditional security would allow applications to run unless they were specifically blocked or security software flagged the process. Zero trust uses application whitelisting so only approved applications are allowed to run.
Examples of Zero Trust Security in action
-
On a company owned computer, files can be downloaded. The same user account can only view files on a non-company owned device. The user and the machine's identity combine to determine access.
-
Office 365 data can be wiped from a terminated employees personal phone without disturbing that persons personal data
-
A computer that is missing a patch is blocked from downloading new emails in Outlook
-
A word document with a SSN in it is blocked and a copy is sent to the corporate compliance officer
Proud to be local. Areas we serve in Ohio:
Zero trust can take a lot of time to setup. The users, computers, applications and servers have to continue working while they are reconfigured. This is where an Managed Service Provider can help. Internal IT department employees may go through an implementation once or once every two to three years as they change jobs. An MSP employee may be a part of three different implementations in the same month. Experience matters.
With additional data comes additional decisions. Instead of just assigning access to a username there must now be a policy for a user + a type of computer + a location + a time of day.
Legacy systems rely on “implicit trust”; this concept conflicts with the core principle of adaptive evaluation of trust in the new model. Committing to Zero Trust may require certain applications to be upgraded or replaced. Progress sometimes requires large investments.
